Share :
RedTeam missions

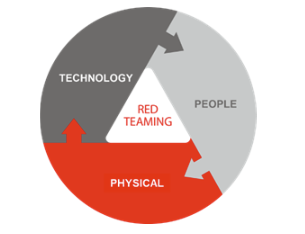
Synetis carries out so-called “RedTeam” missions. This type of attack aims to simulate the point of view of an external, motivated attacker, whose goal is to break into your organization’s network in order to carry out sabotage operations, steal strategic data, install ransom or even persistence software, etc. The Synetis methodology relies on three paths to access the organization’s IS: the computer path (logical intrusion), the cognitive path (social engineering) and the physical path (physical intrusion). These three paths can be used in parallel using a suitable methodology.
More specifically, the Redteam mission provides answers to the following questions:
- What sensitive target data can be obtained from the Internet?
- Are employees sufficiently aware of social engineering practices (phishing, spear-phishing)?
- What are the consequences of losing or stealing a company laptop?
- What compromises are possible from within the company (malicious employees, etc.)?
The approach is different from the “classic” approach: the auditor will take on the role of an attacker and, unlike a classic approach where he or she will attempt the more tests possible in order to test the audited perimeter as much as possible, it will be as stealthy as possible to reach the defined trophies, so as not to be detected by the target’s detection capabilities.
The RedTeam approach aims to simulate realistic (non-destructive) attacks, to thoroughly test the security of a given perimeter. This approach makes for greater efficiency and enables advanced attack scenarios (logical intrusion, social engineering, phishing, etc.).
The RedTeam is trophy-oriented predefined jointly by the auditors and the customer (access to the back-office of an e-commerce site, to a customer database, exfiltration of a CRM database, obtaining Domain Admin access, compromising AD, detecting the use of a ghost account, access to a VIP’s mailbox, access to an ERP, etc.). These trophies, contextualized, allow us to concretely illustrate real risks that can impact the client. Obtaining these trophies validates the feasibility and the exposure of the client to the said risks.
As a result, a Redteam approach is not intended to be the most exhaustive in terms of security testing against assets (unlike a “classic pentest”), but is oriented towards a global, tactical and efficient compromise in order to get as close as possible to the real trophy attacks.
One of the objectives is also to define for an organization the impact of a real attack and the cost of the associated measure.
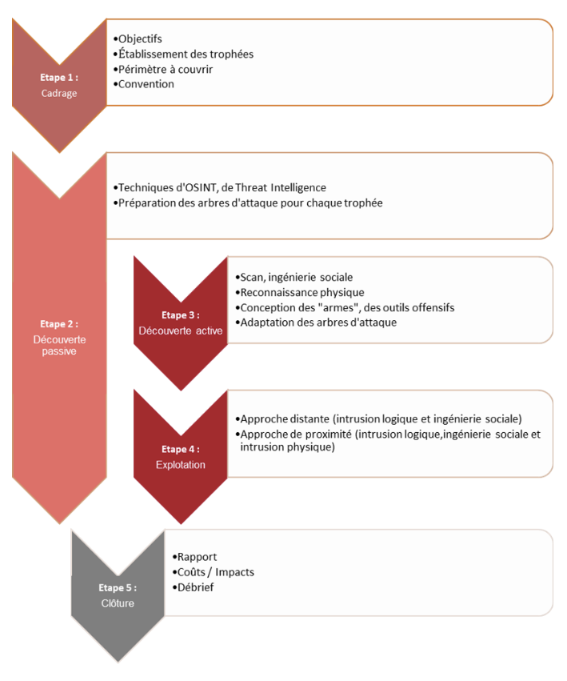
As part of its Red Team missions, Synetis may be required to use up to three different channels: the IT channel (logical intrusion), the cognitive channel (social engineering) and the physical channel (physical intrusion).
Mainly remote, this approach aims to identify the external perimeter of the information system and exploit potential vulnerabilities to gain access to the organization’s internal network. There are three distinct phases:
- Open-source intelligence phase, which focuses on gathering and analyzing information about the target organization in order to deduce a scope that will be validated and/or refined as the mission progresses: physical sites, employees, partners, service providers, information leaks (internal reports, passwords, etc.), information system (public addressing plan) ;
- Discovery phase of the external surface of the information system, aimed at mapping the infrastructures accessible from the Internet: exposed services, technologies used, security equipment..;
- Offensive testing phase on external services, aimed at breaking into the organization’s DMZ by compromising front-end servers, then bouncing back onto the internal network.
The aim of this approach is to exfiltrate authentication information or gain access to the organization’s internal network by exploiting phishing techniques, for example. There are three distinct phases:
- Profiling phase, to identify a list of people to target for the phishing campaign and gather as much information as possible to develop relevant scenarios;
- Definition of phishing campaign scenarios (e.g., sending an e-mail inviting the victim to visit a URL to enter his or her credentials, or to download a malicious file containing a backdoor);
- Campaign implementation, e.g. sending e-mails, collecting indicators (statistics on reception/reading of e-mail/opening of malicious link) and obtaining access (backdoor or logins).
The aim of this approach is to gain access to the organization’s internal network via a proximity approach that may even involve physical intrusion into the organization’s premises (head office or subsidiary, for example):
- Active reconnaissance phase: perimeter discovery of premises/employees, identification of surrounding wireless networks and offensive tests against them, garbage can searches, deposit of malicious USB keys, etc. ;
- Physical intrusion and placement of an implant on the internal network to gain remote access (Wifi or 4G antenna);
- Offensive tests on the internal network.
At the end of this exercise, which may last several weeks, the list of vulnerabilities will be drawn up by Synetis auditors, along with an action plan. Synetis undertakes to restore the information system to the same state as before the beginning of the financial year.
Synetis’ Redteam methodology is described below (where phase 2 is carried out continuously throughout the service):