Governance, Risk and Compliance
Organizing, framing and accompanying
risks and cybersecurity!
GRC
the three inseparable pillars to help you achieve your cyber goals.
GRC stands for “Governance, Risk Management and Compliance”, and is an umbrella term for how organizations manage the three pillars that help them achieve their cyber-security objectives.
As a business, CRM’s main role is to create a synchronized approach to these areas, avoiding duplication of effort and ensuring the effectiveness andefficiency of the approaches used.
In a 4th pillar, we have added business continuity planning andorganization activities, for complete coverage of risks and challenges.
Use cases and value.
ORGANIZATION
● Set up a cross-functional safety management system;
● Define requirements and support their achievement.
COCKPIT
● Manage safety projects to ensure consistency and rationalize actions;
● Ensure their efficiency in relation to key issues.
RISK MANAGEMENT
● Identify sensitive and valuable data and measure their risk exposure ;
● Providing tailored solutions to optimize efficiency.
Decision support
● Provide decision-makers and management with objective, verifiable and measurable assessment data to help them make the right decisions;
● Highlight the challenges and benefits of safety.
Supervision
● Identify scenarios and use cases for monitoring devices, as well as the threats to be monitored;
● Independently design and implement organization-wide controls.
A risk-oriented approach.
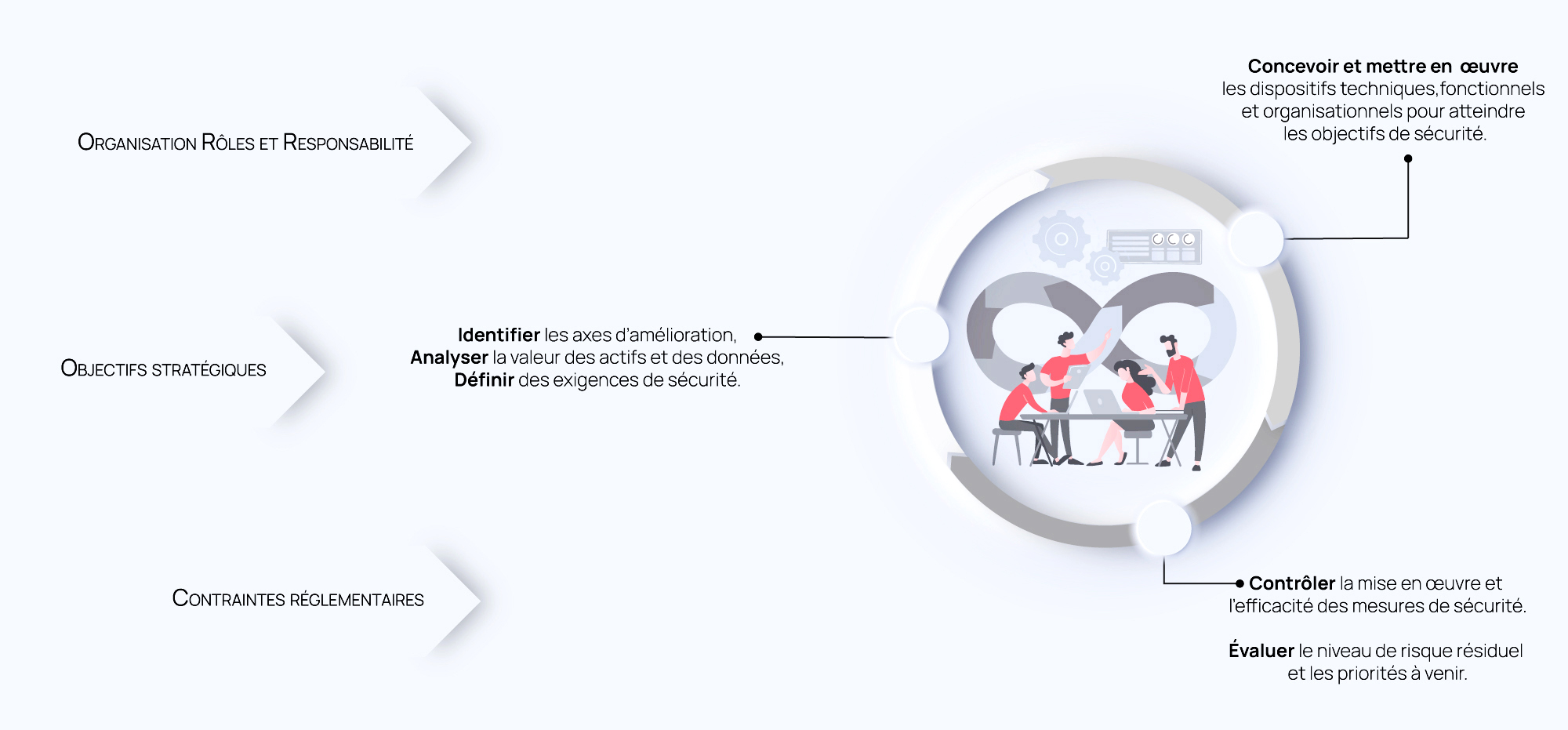
Our areas of expertise.

Defining governance strategy and building security :
Based on your organization’s strategy and challenges, our information security consultants help you define your projects, identifying the security objectives and associated cyber risks for each one (operational challenges, regulatory framework, image and reputation preservation, etc.).
Our experts analyze your practices, whether documented or presented during interviews and educational workshops, and perform cybersecurity maturity diagnostics. Your practices are benchmarked against best practice, enabling you to develop your security policies and systems, whether technical, organizational or functional.
A master plan in the form of roadmaps is then drawn up in collaboration with all the teams involved. The latter gives you a short- and medium-term vision, with a 3-year horizon.
To support the implementation of this roadmap and bring your organization’s security department to life on a day-to-day basis, an experienced consultant can be seconded to support the existing security team, or as a part-time CISO.
Identify, analyze and manage risks.
In order to gain a complete picture of your exposure to cyber threats and attacks, a risk analysis is carried out within your organization. This mapping of “corporate” and “business” risks provides a decision-making tool enabling decision-makers to arbitrate issues on a case-by-case basis, and thus implement a risk management plan with appropriate, relevant and proportionate corrective actions.
With the help of pragmatic methodologies (in particular, the EBIOS Risk Manager method designed by ANSSI), all of these projects can be integrated into a “security by risk” approach that, through an iterative and agile strategy, makes it possible to address the issues that need to be addressed at the right time and with the right resources.
Risk management also integrates safety at the heart of projects, in both build and run. With this approach, security milestones are integrated into the project lifecycle, with the aim of identifying risks at the design stage and integrating security requirements into the specifications.
Finally, a long-term risk management system can be set up to provide a tool for monitoring risk and safety, keeping the risk treatment plan alive and up-to-date, and keeping the risk analysis up to date.
Targeting and assessing compliance :
Backed by a proven methodology, we support companies in bringing their organization into compliance with a wide range of standards, directives, laws and regulations (ISO 27001, NIS2, LPM, NIST, SecNumCloud, PASSI, DORA, PCI-DSS).
The first step towards compliance is to carry out a full audit, analyzing practices and documentation, identifying discrepancies and non-conformities, and documenting the actions to be taken.
For each compliance standard, a detailed roadmap and action plan is then delivered. We are able to offer comprehensive, tailor-made support, drawing on all the strengths and skills of Synetis experts, right through to certification or homologation, if required. Finally, compliance monitoring tools such as dashboards can be set up and configured by our experts.
Cyberattack, fire, damage, theft, climatic events, geopolitical crisis: more than ever, organizations need to be ready to deal with a crisis situation. To achieve this, our cybersecurity experts can help you develop business continuity and IT continuity strategies, and prepare for crisis management.
Operational continuity: By establishing an operational continuity strategy, your teams are able to maintain business activity, and the organization can adapt in the face of an unprecedented event. By adopting a resilient posture, a system for operating in downgraded mode (generalized remote working, back-up equipment) accompanied by communication resources and team support systems will be put in place to deal with the situation.
IT continuity: By first analyzing the company’s day-to-day operations, value chains and critical business assets are identified. For each of these assets, a continuity objective is established, including the maximum acceptable time to rebuild the asset and the level of associated data logging required for operation in degraded mode.
Preparing for a crisis: In the event of a crisis, the first moments are crucial. So that you can be responsive and efficient, our teams can help you develop a tailor-made crisis management system: definition of the decision-making chain, crisis governance, directories, regulatory formalities, preparation of internal and external communications…
Last but not least, we organize full-scale exercises to prepare you for a major event, so that you don’t give in to emotions during a crisis, and so that you can put your systems to the test and get trained.
Our strengths.
Made-to-measure service
We build an approach and methodology specifically adapted to your context and challenges, to precisely address and meet your needs.
Flexibility & adaptability
As each assignment progresses, we take all the feedback into account, adapting our approach as necessary to meet changing needs.
experience
Our consultants have an average of 6 years' experience in GRC, and have worked on a variety of assignments. All managed and supervised by senior consultants and managers.
commitment
Our top priority is to deliver results and quality. All our teams are fully mobilized, from consultants to management.
Dedicated offensive training.
Synetis can provide your staff with training on a wide range of subjects linked to the major theme of cybersecurity, backed up by R&D and feedback from our consultants.
Offensive training courses vary in length. Most take place over one day, but some can extend to 3 or 5 days, enabling Synetis consultants to tackle each theme in full, and provide participants with all the keys they need to understand and assimilate the training.
In terms of cybersecurity training, the GRC catalog includes :
Click here
click here
the complete training link
Our experts have the answers.
These answers offer a general overview of the practices that might be found in an organization to manage cybersecurity and GRC.
Tailored to your company's specific needs, they can form a solid basis for reinforcing your overall security posture.
Governance processes should include setting up an IT security committee, defining cybersecurity policies, appointing an information security officer, and regular reviews to ensure compliance with governance guidelines.
It is important to use an approach based on continuous identification of vulnerabilities, periodic risk assessment, and a mitigation strategy involving technical, organizational and human measures.
Ongoing training programs can be set up to raise employee awareness of cybersecurity threats. This can include simulated phishing exercises, regular training sessions and the dissemination of security information.
An incident management plan is required, detailing the procedures to be followed in the event of a security breach. Incident simulations can be carried out regularly to test the effectiveness of the response and make ongoing improvements.
Ongoing training programs can be set up to raise employee awareness of cybersecurity threats. This can include simulated phishing exercises, regular training sessions and the dissemination of security information.
An incident management plan is required, detailing the procedures to be followed in the event of a security breach. Incident simulations can be carried out regularly to test the effectiveness of the response and make ongoing improvements.





